Research Article - (2024) Volume 1, Issue 1
Growler & Panther Under the Influence of Electronic Warfare
Received Date: Oct 28, 2024 / Accepted Date: Dec 04, 2024 / Published Date: Dec 16, 2024
Copyright: ©2024 Muhammad Farhan Shahid. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Citation: Shahid, M. F. (2024) Growler & Panther Under the Influence of Electronic Warfare. Ther Res: Open Access, 1(1), 01-05.
Abstract
In this study, I explore the three sub-categories of Electronic Warfare (EW): Electronic Attack (EA), Electronic Protection (EP), and Electronic Support (ES), and provide a comparative analysis of base variants of Boeing EA-18G Growler and the F-35 Lightning II aircraft. This brief comparison underscores the complementary nature of these aircraft in electronic warfare domain, illustrating how their distinct strengths contribute in achieving air superiority and mission success in complex operational environments.
Introduction
Electronic Warfare (EW) is the term used to define ability of exploitation of electromagnetic spectrum in order to detect and interpret enemy EM signals for subsequent disruption or protection of military assets in certain war scenario [1].
Sub-Categories of Electronic Warfare Following are the three sub categories of electronic warfare
• Electronic Support (ES) / Electronic Support Measure (ESM)
• Electronic Attack (EA) / Electronic Counter Measure (ECM)
• Electronic Protection (EP) / Electronic Counter Counter Measure (ECCM)
1.1. Electronic Support Measure (Esm)
Electronic warfare support (ES) is a subdivision of EW field where electronic intelligence is gathered through passive listening. This is often referred to as reconnaissance and sometimes can be employed for early warning as well. ESM system is capable of detecting EM radiations emitted from an enemy electronic transmitter typically radar or communication equipment. It can record signals for subsequent analysis and interpretation which is used for EOB build–up and R&D purpose. ESM can be further broadly divided according to role and task of ES mission [2].
a. SIGINT (Signal Intelligence). SIGINT is the passive listening and recording of EM signatures through surface, sea or aerial platform.
• ELINT (electronics intelligence). For gathering information of airborne or ground radar signatures.
• COMINT (communications intelligence). For gathering information of airborne or ground communication channels / links signatures and transmission over it.
b. Tactical ESM. Purpose of this ESM is to intercept, identify and locate sources of radiated electromagnetic energy for immediate threat recognition such as warning missile approaching to an aircraft. Actions are carried out by operational commander for taking swift decisions.
1.2. Capabilities of Esm
ESM system can measure the parameters of the incoming radar signal / comm. Signals in the operating frequency range. The typical parameters that can be measured are Pulse width (PW), Pulse repetition frequency (PRF), signal power, time of arrival (TOA), the direction of arrival (DOA). It can further locate the estimated position of target through TOA techniques.
1.3. Electronic Attack (Ea) / Electronic Counter Measure (Ecm)
Electronic attack (EA) was previously known as electronic countermeasures (ECM) is meant for offensive use of electromagnetic signals to gain the Spectrum Dominance in anycombat environment. It may involve use of energy weapons or anti-radiation weapons to degrade either temporarily or permanently enemy electronic sensors (radars and communication equipment).2 EA can be employed from air, sea, land, and space and can target various Spectrum Dependent Systems. It can further be categorised based on intention of use as per following details:-
• Active Jamming (Offensive). Transmission of high power signals on side lobes of target emitter (communications systems or radar systems) on nearly same emitting parameters can cause jamming effect which distorts communication or radar reception thus denying use of EM spectrum efficiently [3].
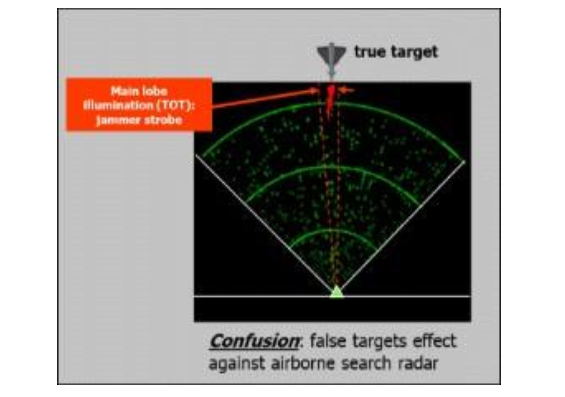
Figure 1: Deceptive Jamming Against
• Active Jamming (Defensive). Actions taken to protect aircraft or ground platform to counter incoming guided missile through jamming of missile terminal homers. It has also been deployed by military ships and recently on some advanced tanks to fool laser / IR guided missiles like self protection jammer (SPJ.)
• Passive Jamming. Such jamming includes chemical or mechanical means and techniques to misguide missile or blind surveillance radar. Chaff dispersion act as medium modifiers between radar and aircraft. Likewise corner reflectors and RAM (Radar absorbing Materials) act as reflectivity modifiers.
1.4. Electronic Protection (Ep) / Electronic Counter Counter Measure (Eccm)
Electronic protection (EP) involves measures used to protect against an enemy electronic attack (EA) or unintentional interference from friendly deployed system. There are two broad classes of EP techniques:-
• Electronic Techniques. These techniques are incorporated in electronic system during design phase. Most surveillance and

Figure 2: Deceptive Jamming Against Airborn Radar Ground Radar
• Deception. After interpreting enemy emissions from target emitter (communications systems or radar systems), signals are retransmitted with additional modulations (frequency, time) superimposed causing enemy systems to acquire and track invalid targets. It can make the real target appear to disappear or move about randomly on enemy C2 console. tracking radars are equipped with a suitable blending of EP techniques which are meant for the following:-
• Prevention of radar saturation.
• Enhancement of signal-to-noise or signal-to- jamming ratio.
• Discrimination of directional interference/ SLS (sidelobe suppression)
• Rejection of false targets / CFAR (constant false alarm rate)
• Maintenance of target tracks.
• Counteraction of ESM, and radar system survivability.
• Operational Doctrines. Exploitation and efficient employment of ECCM features at the right time against the right system is developed through a well-established doctrine. This includes but not limited to the followings:-
• Employing frequency agility/Spread Spectrum technique
• Use of restricted frequencies/Freq change plan
• Emissions control (EMCON) policy
• Low observability (stealth) techniques
• Deployment of Active Radar Decoys
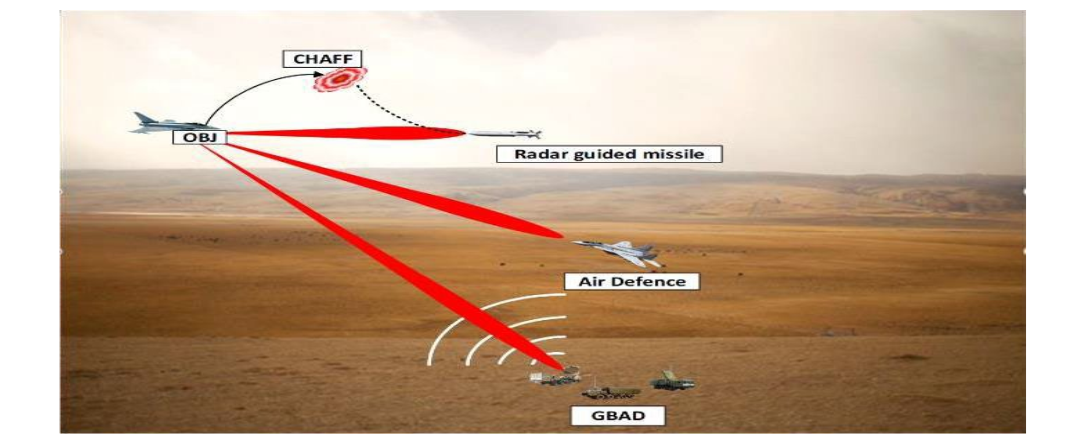
Figure 3: Typical Scenario of Electronic Attack and Protection
Discussion
After retirement of EA-6B Prowler aircraft in March 2019, EA- 18G Growler a derivative of F/A-18 Hornet was developed as a replacement. The primary missions of the aircraft are electronic attack (EA) and suppression of enemy air defense (SEAD). Lockheed Martin F-35 is also equipped with electronic warfare and intelligence, surveillance, and reconnaissance capabilities. However, primary role of this stealth multirole combat aircraft is to perform air superiority and strike missions.1 Detailed equipment segregation on both aircraft as per overt sources is tabulated below.
2.1. Flight & Strike Essentials
Essential equipment ensures not only the aircraft’s functionality but also its survivability. Without reliable avionics, radar systems, and electronic warfare suites, an aircraft would be vulnerable to enemy threats. Additionally, quick maneuvering—enabled by responsive flight control systems, aerodynamic design, and powerful engines—allows pilots to evade incoming missiles, engage adversaries effectively, and maintain air superiority. In the dynamic environment of aerial combat, these systems are essential for both offense and defense role. Table I enlists the basic specification of two state-of-the-art machines which play crucial role for fighter flying [4-5].
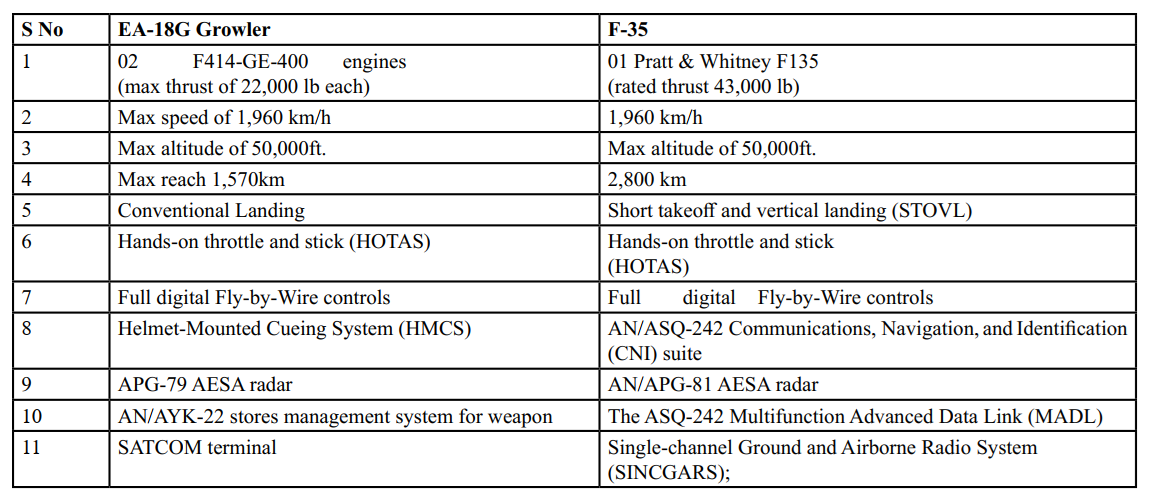
Table I: Basic Specifications and Essential Equipment
2.2. EW Capabilities
In the realm of modern warfare, electronic systems serve both as weapons and vulnerabilities. Fighter jets like the EA-18G Growler and the F-35 Lightning II recognize this dual role. Beyond dogfights and precision strikes, these aircraft must dominate the electromagnetic spectrum.6 The Growler, born from the F/A 18F Super Hornet lineage, suppresses and dismantles enemy air defenses, radar systems, and communication networks. Armed with advanced jamming equipment, it disrupts adversary electronics with surgical precision. Meanwhile, the F-35 seamlessly integrates electronic warfare capabilities into its multirole mission. Table II depicts comparative systems owned by two aircraft which may change EW dominance if employed tactically.
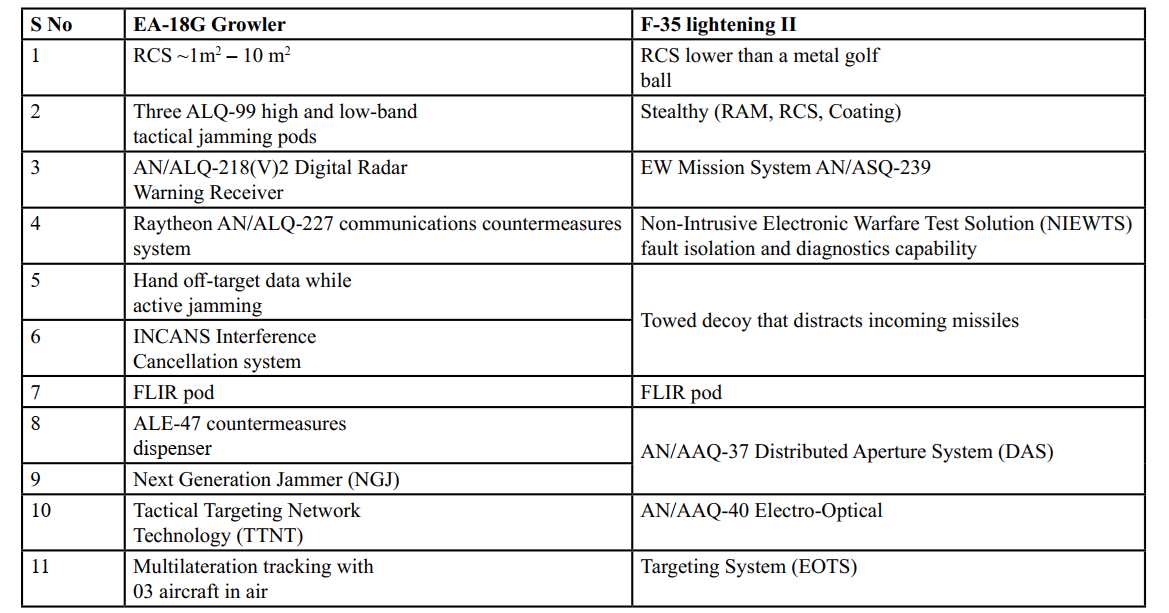
Table II: EW Related Equipment and Specification
2.3. Weaponry Support
Beyond the technical specifications and electronic warfare equipment, the ability to carry and launch a diverse array of weapons and missiles is pivotal for achieving air superiority. Table III enumerates some of the major weapons that both beasts of the sky can support.
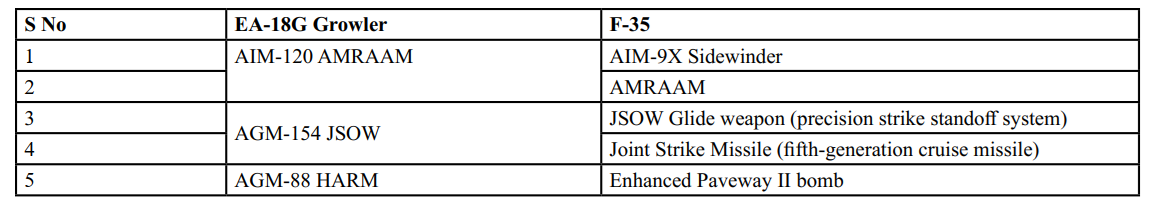
Table III: Comparison of Weapon System Support
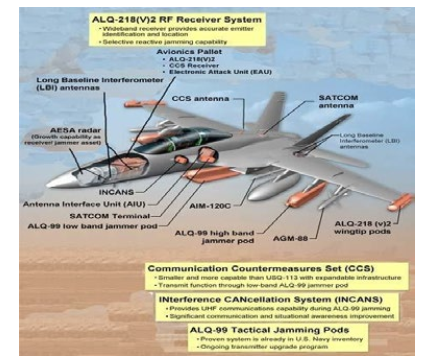
Figure 4: EA-18G EW systems
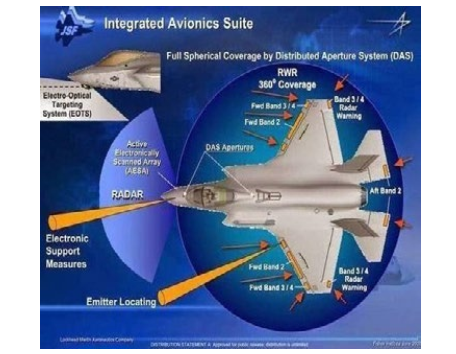
Figure 5: F-35 EW & Avionics systems
2.4. EW Analysis
EA-18 Growler has reportedly scored the simulated aerial victory against the F-22 Raptor (fighter like F-35) in Red Flag or Sim exercises. The EA-18G Growler is purpose-built for electronic warfare. Armed with the ALQ-99 high and low-band tactical jamming pods, it can significantly degrade the radar performance of adversaries like the F-35 from long range. Reliability of ALQ 99 is however questionable due to higher fault rate. Even than if it is successful in jamming AI of F- 35, it will make itself vulnerable and be detected by AN/ASQ-239 EW suite which can identify, monitor, analyze, and respond to threat [4, 5].
The F-35 Lightning II boasts advanced countermeasures. It can f ly closer to the Growler, launching AIM-120D missiles that home in on jamming signals. The F-35’s Distributed Aperture System (DAS) and Electro-Optical Targeting System (EOTS) provide additional situational awareness, enhancing its ability to engage threats.
The Growler faces a dilemma: it must balance active jamming with evading the F-35’s AIM-120 missiles. To counter the F- 35’s BVR active radar, the Growler may need to manoeuvre enough to drain battery and induce energy by diving into thicker air. In parallel, it may utilize its second jamming pod. However, this compromises its ability to jam the F-35’s AI, forcing it to manoeuvre and escape from incoming missiles [6].
6Growler is however able to present different challenge to F-35. While actively jamming, it can share off-target data with other friendly fighters or ground-based air defense (GBAD) systems. This collaborative approach leverages the Growler’s electronic warfare capabilities to benefit the overall battle strategy.
In such combat scenario, the F-35’s superior agility, advanced sensors, and missile capabilities give it an edge. However, the Growler’s electronic warfare expertise and ability to collaborate with other assets make it a formidable opponent.
Conclusion
Ultimately, the outcome of such engagements is influenced by a multitude of factors, including strategic planning, tactical execution, and the skill of the pilots. While the F-35’s superior agility, advanced sensors, and missile capabilities provide it with a distinct edge in air superiority, the Growler’s expertise in electronic warfare and its collaborative potential make it a formidable adversary. The effectiveness of each platform is not determined by technology alone but by how well strategies are crafted, tactics are executed, and pilots leverage their training and experience. These human elements often tip the balance in high stakes aerial combat, highlighting the intricate dynamics at play in achieving air dominance.
References
1. Sharma, P., Sarma, K. K., & Mastorakis, N. E. (2020). Artificial intelligence aided electronic warfare systems-recent trends and evolving applications. IEEE Access, 8, 224761 224780.
2. Maini, A. K. (2018). Handbook of defence electronics and optronics: fundamentals, technologies and systems. John Wiley & Sons.
3. Electronic warfare in the information age, david l. Adamy, artech house, 2015. The f-35 lightning ii: a comprehensive guide, bill sweetman, hachette uk, 2018.
4. Lawrence, D. L. (2000). Army Aviation as an Element of Airpower. US Army War College.
5. Ball, R. E. (2003). The fundamentals of aircraft combat survivability: analysis and design. American Institute of Aeronautics and Astronautics. 6. Rose, L. A. (2007). Power at Sea: A violent peace, 1946-2006 (Vol. 3). University of Missouri Press.



